Website security headers are crucial for protecting your site. They safeguard against various cyber threats.
Security headers provide an extra layer of protection for your website. They help prevent attacks like cross-site scripting (XSS) and clickjacking. With cyber threats on the rise, understanding these headers is essential. They enforce rules that browsers must follow when handling your site’s content.
This ensures a safer experience for your users. In this post, we’ll explore what website security headers are and how they work. We’ll also explain why they are important for your site’s safety. Stay tuned to learn more about securing your website effectively.
Security headers are directives utilized by web applications to configure the security defenses of web browsers. In response to these directives, browsers can make it more difficult to exploit client-side vulnerabilities such as Cross-Site Scripting and Clickjacking. Additionally, headers can be used to configure the browser to only permit valid TLS communication and enforce valid certificates, or even to require the use of a particular server certificate.”
Table of Contents
ToggleIntroduction To Website Security Headers
Website security is a crucial aspect of maintaining a safe online presence. One important element of web security is the use of security headers. These headers are essential for protecting websites from various threats.
Importance Of Security Headers
Security headers help safeguard your website from common attacks. They set rules that browsers must follow. This adds an extra layer of protection. For example, security headers can prevent cross-site scripting (XSS) attacks. They also protect against clickjacking and other threats.
Without these headers, your website is more vulnerable. Hackers can exploit these vulnerabilities. This can lead to data breaches and other issues. Implementing security headers is a simple yet effective way to boost your site’s security.
Basic Concepts
Security headers are part of the HTTP protocol. They instruct the browser on how to handle your website’s content. Some common security headers include Content-Security-Policy (CSP), X-Content-Type-Options, and Strict-Transport-Security (HSTS).
The Content-Security-Policy header controls which resources the browser can load. This reduces the risk of XSS attacks. The X-Content-Type-Options header prevents the browser from interpreting files as a different MIME type. This helps avoid certain types of attacks.
The Strict-Transport-Security header ensures that the browser always uses HTTPS. This secures the communication between the user and the website. Each of these headers plays a unique role in securing your website. Understanding and using them can greatly enhance your site’s security.
Common Security Headers
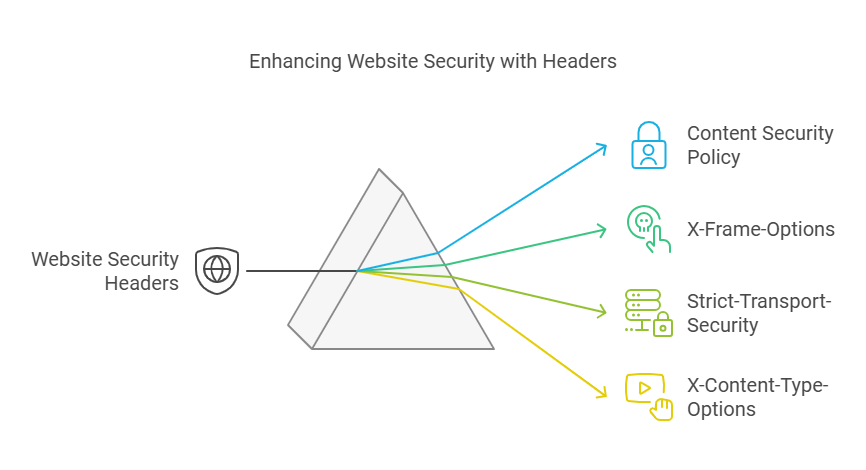
Website security headers are crucial for protecting your site from common threats. They provide an extra layer of security by instructing browsers on how to handle your site’s content.
Let’s explore some common security headers that can help safeguard your website.
Content Security Policy
The Content Security Policy (CSP) header helps prevent cross-site scripting attacks. It does this by allowing you to control the sources from which content can be loaded. By specifying trusted sources, you reduce the risk of malicious scripts running on your site. This makes your website more secure against attacks.
The X-Frame-Options header protects your site from clickjacking attacks. Clickjacking tricks users into clicking on something different from what they perceive. This header controls whether your site can be embedded in frames or iframes on other websites. By setting it to “DENY” or “SAMEORIGIN,” you can prevent unauthorized framing of your content. This keeps your site and users safe.
The X-Content-Type-Options header stops browsers from interpreting files as a different MIME type. This helps prevent certain types of attacks, such as drive-by downloads. By setting this header to “nosniff,” you ensure that browsers only render files with the correct MIME type. This adds an extra layer of protection to your website.
Content Security Policy (CSP)
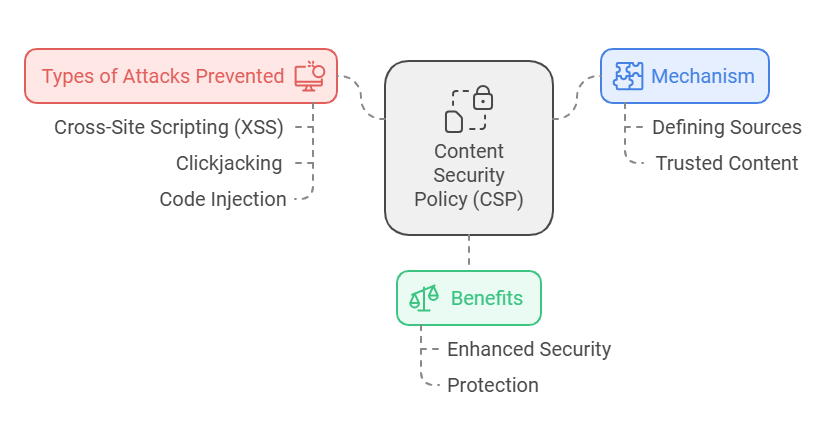
Content Security Policy (CSP) is a powerful tool to enhance the security of a website. It helps protect against various attacks such as cross-site scripting (XSS), clickjacking, and other code injection attacks. By defining the sources from which content can be loaded, CSP ensures that only trusted content is executed on your website.
Purpose Of Csp
The primary purpose of CSP is to mitigate and report certain types of attacks. These attacks include XSS and data injection. CSP does this by restricting the resources (like scripts, styles, and media) that can be loaded on the webpage. This helps in preventing malicious code from being executed.
Implementing a CSP involves defining a set of rules. These rules dictate the content sources that are allowed. For example, you can specify that scripts should only be loaded from your own domain. This significantly reduces the risk of malicious scripts being executed.
Implementation Tips
Here are some tips for implementing CSP effectively:
- Start with a report-only mode: This allows you to monitor the effects of your CSP without enforcing them. It helps in identifying potential issues without breaking the site’s functionality.
- Define strict policies: Specify only trusted sources for your content. Avoid using wildcards like ‘‘. This ensures only specific, trusted content is executed.
- Use nonce or hash: For inline scripts, use a nonce or hash. This ensures that only the scripts you intend to run are executed.
- Regularly review and update: Regularly review and update your CSP. This ensures it remains effective against new threats.
Here is an example of a basic CSP implementation:
Content-Security-Policy: default-src 'self'; script-src 'self' https://trusted.cdn.com; style-src 'self' https://trusted.cdn.com;In this example:
- ‘default-src ‘self’;:
- Allows content only from the same origin.
- ‘script-src ‘self’ https://trusted.cdn.com’;:
- Specifies that scripts can only be loaded from the same origin and a trusted CDN.
- ‘style-src ‘self’ https://trusted.cdn.com’;:
- Specifies that styles can only be loaded from the same origin and a trusted CDN.
By following these tips, you can effectively implement CSP and enhance your website’s security.
X-frame-options
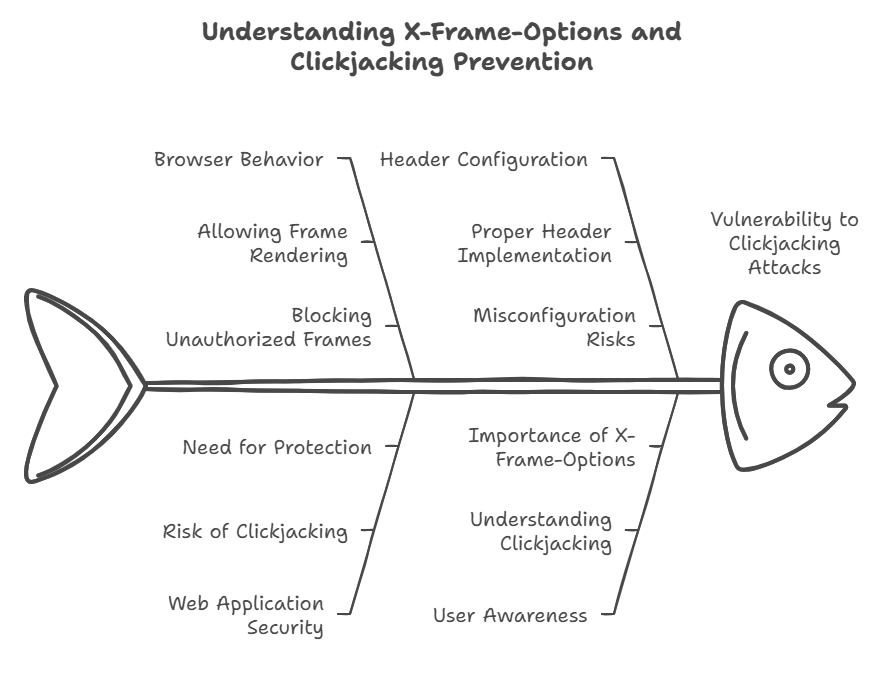
The X-Frame-Options header is a crucial part of website security. It protects web applications against clickjacking attacks. This header controls whether a browser should be allowed to render a page in a or not. Let’s explore how it works.
Clickjacking Prevention
Clickjacking is a malicious technique. It tricks users into clicking on something different from what they intend. A hacker overlays a transparent over a legitimate button on a website. When users click the button, they unknowingly perform actions on another website.
The X-Frame-Options header prevents this. It ensures your web page can’t be embedded into frames from other domains. This protects users from these deceptive attacks.
Different Directives
The X-Frame-Options header supports three directives:
DENY: Prevents any domain from framing the content.SAMEORIGIN: Allows the page to be framed only by the same origin.ALLOW-FROM uri: Permits framing from a specified URI.
Here’s an example of each directive in use:
| Directive | Usage Example |
|---|---|
DENY | X-Frame-Options: DENY |
SAMEORIGIN | X-Frame-Options: SAMEORIGIN |
ALLOW-FROM uri | X-Frame-Options: ALLOW-FROM https://example.com |
Implementing these headers is simple. It involves adding the correct directive to the HTTP response.
Here’s an example of how to set the X-Frame-Options header in Apache:
Header set X-Frame-Options "SAMEORIGIN"
For Nginx, use the following configuration:
add_header X-Frame-Options "SAMEORIGIN";
By using the X-Frame-Options header, you protect your website from clickjacking threats. It’s a simple yet effective security measure.
X-content-type-options
Website security headers are critical for protecting your site from various threats. One such header is the X-Content-Type-Options. This header safeguards against MIME-type attacks, which can compromise your website. Setting this header helps ensure that browsers handle files in a secure manner.
Mime Type Sniffing
MIME-type sniffing is a browser feature that guesses the type of file being loaded. This can be risky. If a browser misinterprets a file, it could execute malicious code. The X-Content-Type-Options header prevents this by instructing the browser to stick to the declared content type.
For example, if a file is labeled as a text file, it will be treated as such. This stops attackers from embedding harmful scripts within files like images or documents. It enhances security by reducing the risk of MIME-type attacks.
Configuration Guide
Configuring the X-Content-Type-Options header is straightforward. You can add it to your web server configuration. For Apache, you would add the following line in your .htaccess file:
Header set X-Content-Type-Options "nosniff"For Nginx, include this line in your server block:
add_header X-Content-Type-Options "nosniff";Setting the header to “nosniff” tells the browser not to guess the MIME type. This simple step can greatly improve your website’s security posture.
HTTP Strict Transport Security (hsts)
HTTP Strict Transport Security (HSTS) is a web security feature. It ensures your website only uses HTTPS connections. This helps protect against attacks like man-in-the-middle attacks. HSTS tells browsers to only connect to your site using HTTPS. This makes browsing safer for users.
Enhancing Https
HSTS greatly enhances the security of HTTPS. It forces browsers to use secure connections. This helps to prevent data from being intercepted. Users are protected from certain types of cyber attacks. Using HSTS shows a commitment to user safety.
Deployment Best Practices
Deploying HSTS is simple but must be done carefully. Start with a short max-age directive. This allows testing of the HSTS policy. Gradually increase the max-age value. Ensure all subdomains are included with the includeSubDomains directive. Use the preload directive to submit your site to the HSTS preload list. This ensures browsers enforce HSTS even on the first visit.
Referrer-policy Header
The Referrer-Policy header is a security feature for web developers. It controls how much referrer information browsers share during navigation. This header can help protect user privacy and improve security. Let’s dive deeper into this important header.
Control Over Referrer Information
Browsers send referrer information during requests. This information tells the destination website where the request came from. Sometimes, this can reveal sensitive data. The Referrer-Policy header gives you control over this process. You can decide what information gets shared.
Policy Options
The Referrer-Policy header offers several options. Each option controls the amount of information shared.
no-referrer: No referrer information will be sent.
no-referrer-when-downgrade: Referrer info is sent to secure sites only.
same-origin: Referrer info is sent to the same origin only.
origin: Only the origin part of the URL is sent.
strict-origin: The origin is sent only to secure sites.
origin-when-cross-origin: Full URL for same-origin, origin only for cross-origin.
strict-origin-when-cross-origin: Full URL for same-origin, origin only for secure cross-origin.
unsafe-url: Full URL is sent with all requests.
Choosing the right option depends on your site’s security needs. Each option provides a different level of control and privacy.
Best Practices For Security Headers
Implementing security headers is critical to protect your website from vulnerabilities. They provide an extra layer of defense. Following best practices for security headers ensures your site stays secure.
Regular Updates
Security threats evolve constantly. Regularly update your security headers. Keep track of the latest security standards. Use tools to monitor updates. This helps keep your website safe from new vulnerabilities.
Testing And Validation
Always test your security headers. Validate them to ensure they work correctly. Use online tools like SecurityHeaders.com. These tools help identify misconfigurations.
Testing ensures your headers are effective. Validation confirms they are properly set. Regular testing and validation can prevent security breaches.
| Tool | Description |
|---|---|
| SecurityHeaders.com | Test your SSL configuration. |
| SSL Labs | Tests your SSL configuration. |
Follow these best practices for robust website security. Regular updates and thorough testing are key. Stay vigilant to protect your site from threats.
Common Mistakes To Avoid
Implementing website security headers is crucial for website protection. Yet, many developers make mistakes that can leave sites vulnerable. Knowing these common mistakes helps you avoid them and keep your site safe.
Misconfigurations
Misconfigurations are a frequent issue with security headers. These errors often result from:
- Incorrect syntax
- Incomplete settings
- Inconsistent policies
For example, a common mistake is misconfiguring the Content Security Policy (CSP). This policy helps prevent cross-site scripting (XSS) attacks. Misconfigurations can lead to weak defenses, making your site vulnerable.
Ensure your security headers are properly set. Double-check the syntax and completeness. Use tools to validate your configurations. Proper configuration is key to effective security.
Overlooking Compatibility
Overlooking compatibility can cause significant issues. Different browsers and devices may interpret security headers differently. Not testing on multiple platforms leads to problems.
For instance, some security headers might not be supported by older browsers. This can result in reduced functionality or security gaps. Always consider the compatibility of your security headers.
Test your site across various browsers and devices. Adjust your headers as needed. Ensure they work well on all platforms. Compatibility ensures your security measures are effective and do not disrupt user experience.
To avoid these mistakes, stay informed about common pitfalls. Properly configure your security headers and ensure compatibility. These steps will help you maintain a secure and reliable website.
Frequently Asked Questions
What Are Website Security Headers?
Website security headers are HTTP response headers that enhance web application security. They protect against threats like XSS, clickjacking, and more by instructing the browser on how to behave.
Why Are Security Headers Important?
Security headers are crucial because they prevent common web vulnerabilities. They instruct browsers on security policies, ensuring safer interaction and data protection.
How Do Security Headers Protect Websites?
Security headers protect websites by enforcing policies. They mitigate risks like XSS and clickjacking, enhancing browser security and user data protection.
Which Security Headers Should I Use?
Common security headers include Content-Security-Policy, X-Content-Type-Options, and Strict-Transport-Security. Each serves a unique purpose in protecting your website.
Conclusion
Website security headers are crucial for protecting your online presence. They help prevent various cyber threats. Implementing these headers can enhance your website’s security. Start with the basics, like Content Security Policy and X-Frame-Options. Regularly update your security settings to stay protected.
Remember, a secure website builds trust with users. Don’t overlook this vital aspect of web security. Make your site safer today!

